Introduction
Web vulnerabilities can pose significant risks to both website administrators and users. One such vulnerability, CVE-2023-29489, a cross-site scripting (XSS) flaw, has been identified in the cPanel service of the Much Marcle Parish Council website (https://muchmarcleparishcouncil.gov.uk). This medium severity issue affects cPanel versions prior to 11.109.9999.116 and could allow attackers to execute malicious scripts, compromising user data and website integrity. In this blog, we’ll explore the vulnerability, its potential impact, steps to reproduce it, and actionable remediation strategies to secure the Much Marcle Parish Council website.
What is Cross-Site Scripting (XSS)?
Cross-site scripting (XSS) is a security vulnerability that allows attackers to inject malicious scripts into web pages viewed by users. This occurs when a website fails to properly sanitize or validate user inputs, enabling the execution of arbitrary JavaScript code. XSS attacks can lead to serious consequences, including:
-
Session Hijacking: Attackers can steal session cookies to impersonate legitimate users.
-
Data Theft: Sensitive information, such as login credentials or personal details, can be compromised.
-
Website Defacement: Malicious scripts can alter the website’s appearance or redirect users to harmful sites.
-
Malware Distribution: Attackers may use XSS to deliver malware to unsuspecting users.
Technical Details of CVE-2023-29489
CVE-2023-29489 targets the cPanel service, specifically the cpsrvd error page, accessible at https://muchmarcleparishcouncil.gov.uk:2083. The vulnerability arises when an invalid webcall ID is provided, and the application fails to sanitize the input. In this case, an attacker can craft a malicious payload, such as:
/cpanelwebcall/%3Cimg%20src=x%20onerror=%22prompt(document.domain)%22%3EaaaaaaaaaaaaThis payload leverages the onerror attribute of an <img> tag to execute JavaScript code (e.g., prompt(document.domain)) when the image fails to load. This allows attackers to run arbitrary scripts in the context of the user’s session, posing a significant security risk.
How I Discovered a Reflected XSS on the MOD UK Police Website (WAF Bypass)
Steps to Reproduce
To demonstrate the vulnerability on the Much Marcle Parish Council website:
-
Open a web browser and navigate to https://muchmarcleparishcouncil.gov.uk:2083 to access the cPanel login page.
-
Append the following payload to the URL:
/cpanelwebcall/%3Cimg%20src=x%20onerror=%22prompt(document.domain)%22%3Eaaaaaaaaaaaa -
The full URL should look like:
https://muchmarcleparishcouncil.gov.uk:2083/cpanelwebcall/%3Cimg%20src=x%20onerror=%22prompt(document.domain)%22%3Eaaaaaaaaaaaa -
Upon loading, the payload triggers a popup displaying the domain (muchmarcleparishcouncil.gov.uk), confirming the XSS vulnerability.
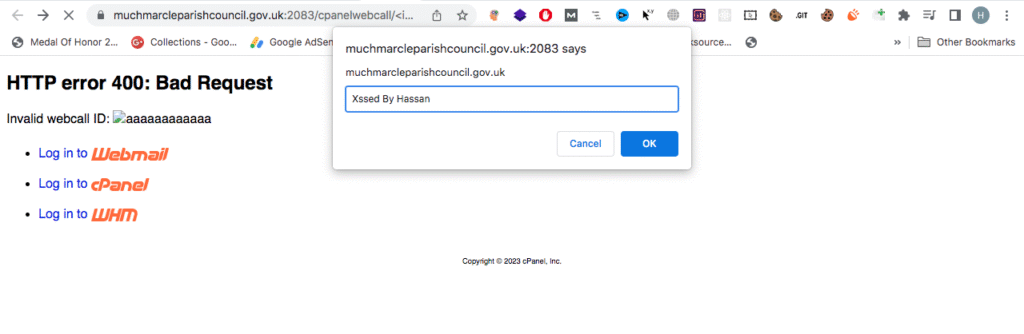
Impact of CVE-2023-29489
The XSS vulnerability in the cPanel service of the Much Marcle Parish Council website could have serious implications:
-
Unauthorized Access: Attackers could steal session cookies, gaining unauthorized access to cPanel accounts.
-
Data Exposure: Sensitive user data, including administrative credentials, could be compromised.
-
Website Integrity: Malicious scripts could deface the website or redirect users to phishing pages.
-
Reputation Damage: A security breach could undermine trust in the Parish Council’s online presence.
Remediation Strategies
To mitigate CVE-2023-29489 and secure website, the following steps are recommended:
-
Apply Security Patches.
-
Implement Input Validation.
-
Secure cPanel Configuration.
-
Conduct Security Training.
-
Perform Regular Security Audits.
-
Monitor and Respond.
The vulnerability has been successfully fixed on https://muchmarcleparishcouncil.gov.uk:2083. Testing the payload no longer triggers the JavaScript execution, confirming that the site is now secure against this XSS flaw.
